The Complete Guide for Risk Assessment in Startups
A short guide for startups that fight to complete a risk assessment for their SOC 2 audit

By Meiran Galis
Please note: this article aims for startups in Seed to Round A and focuses on Security and Operation.
Let's state the obvious: Startups in seed-stage are 100% product-customer oriented. They are doing their best to break into the market, management is working relentlessly and board members measure objectives and performance. It is not surprising that security is not an integral part of their roadmap.
A common case I have experienced often is companies rushing for compliance because a few clients or an S&P 500 corporate want to move forwards with the agreement process but demand security compliance standards. Now the startup needs the SOC2 fast, but things take time, and resources.
You might be surprised to hear that the Risk assessment procedure does not exist nor part of many of my client's roadmap. It might make sense because as I mentioned before, security is still lagging behind and various controls are not in place. Following my experience with advising companies together with their security in-charge employee (various from CISO to CTO, VP R&D, VP Operation or VP Compliance) I notice that they didn't honestly know how to do it, or interested to understand why they needed it.
After dozens of meetings I found myself explaining over and over why startups need a clear Risk Management process (also part of this compliance), and how they can do it (pro-actively managing and tracking). so let's start:
What is Risk?
Risk is the overlap between Assets, Vulnerability, and Threat. In other words, Risk is the probability of the realization of a threat.
Assets – What to protect, where and why. The initial assessment phase starts with the identification of assets in the organization.
It is very important to have a clear view of your assets.
Vulnerability – Vulnerabilities are an internal factor. That's mean that if you know about them, there is certainly something you can do. As a DevOps manager, you are responsible for the security of the production servers. You should have a patch management process for OS, configured auto anti-virus scans, manage shall access and more. As an R&D Manager, you want to check for security review in the requirement phase, implement security into the design, do code reviews, scan the code for vulnerabilities and more. Every Role comes with is own vulnerabilities and own risks.
Threats:
- Adversarial Threats – People or organization trying to break in and hurt your networks or your business. Consider their capability, intent, and likelihood (Trusted insiders, Competitors, Suppliers, Customers, Business partners, Nation-states)
- Accidental Threats: Occurs when someone makes a mistake that hurts the security of the system (System administrator accidentally takes servers offline causing loss of availability)
- Structural Threats: Occurs when equipment, software, or environmental controls fail
- Environmental Threats: Occurs when natural or man-made disasters occur (epidemic, flooding in DC, Fiber or telecommunication lines cut, no electricity, war
Here are the most common Risks list criteria:
- Strategic Risk: Resulting directly from operating within a specific industry at a specific time (business objectives, shifts in consumer preference or new technologies can make your product lines obsolete).
- Compliance Risk: Legislative laws and bureaucratic regulations.
- Financial Risk: Handle money, how do you allow your customers to pay you.
- Operational Risks: Results from internal failures to internal processes, people, or systems (can result from unforeseen external events like a power outage or cyber-attack).
- Reputational Risk: Loss of a company’s reputation or community standing from product failures, lawsuits, or negative publicity.
- Other Risks: Environmental (natural disaster, epidemic), Employee Management (Maintaining a trained staff with up-to-date skills), Political Instability (Change in-laws and regulations).
What Can You Do With Risk?
Its time to choose your mitigation strategy and define the mitigation plan. There are 4 alternatives in which you should consider:
- Risk mitigation: The main goal of security is to minimize risk to an acceptable level (not necessarily to eliminate all risks). By adding risk controls, we can mitigate the risk down to an acceptable level.
- Risk Avoidance: Risk is too high to accept, so the system configuration or design is changed to avoid the risk associated with a specific vulnerability (Utilizing Windows XP is too dangerous, so we install Windows 10 instead to avoid the risk of an unsupported operating system).
- Risk Acceptance: Organization accepts the risk associated with a system’s vulnerabilities and their associated risks. Risk acceptance is common when the risk is low enough to not apply countermeasures, or adequate countermeasures have already been applied. Remember – reactive approaches mean you aware of a risk an choose to accept it and do nothing.
- Risk Transference: If the organization cannot afford to accept, avoid, or mitigate the risk, they can transfer the risk to another business.
Controls are here to help your organization dealing with the risks you identified, understand the problem and construct an effective countermeasure. There are two types of controls:
- Technical controls: Systems, devices, software, and settings used to enforce CIA requirements (Using firewalls, IDS, and IPS. Installing antivirus and endpoint security)
- Operational controls: Practices and procedures to increase security (Utilizing standard operating procedures, do pen test, etc.)
You will need to have both operational and technical control. They support each other. In addition, I constantly recommend automating controls as much as possible and be alerted when an event triggers a predefined rule.
So let's assume you have identified a variety of potential risks, defined a mitigation plan, but how can you tell if anti-virus implementation is more important then vault for secrets and keys? After all, your budget is limited and not always you can afford a managed solution.
Risk Prioritize:
Startups should conduct a qualitative risk measurement due to simplicity. Don't get lost with too much information, just understand the risk level:
You will compare Probability vs. Impact with a rank of
High – highly motivated and sufficiently capable
Moderate – motivated and capable, but controls are in place
Low – lacks motivation or capability, or controls are in place to prevent
Prepare a list with all risks mitigation plan (and strategy), and prioritize them in a board through any project management tool you use (e.g. moday.com, Asana, Trello, or Google Sheet). It's important to collaborate with other, assigned risk owners and set due dates. Track and monitor progress and check your KPIs).
-
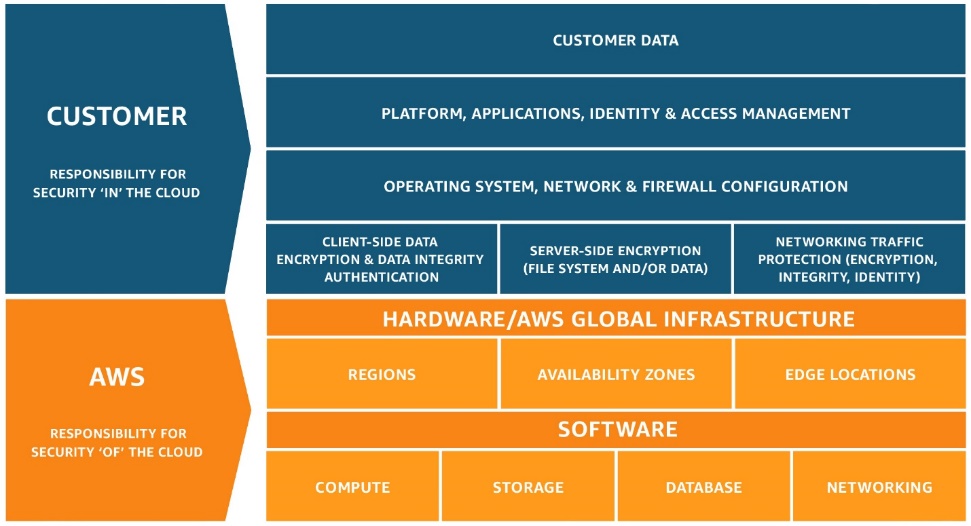
As a CISO, you need to conduct at least annual risk assessments for each department in the organization. Management conducts an annual risk assessment meetings, and it's under your responsibility to present risks and propose solutions and prices. Keep in mind to focus on infrastructure, software, procedure, and people: Infrastructure: hardware and network. If your infrastructure based on a sub-service organization (IaaS provider, e.g. AWS), check on the shared responsibility model: Software: Operating systems, tools, identity management, SIEM, IDS, DLP, Anti-virus, End-points management, configuration and more.
- Procedure: Policies and procedures in multiple domains: Security policy, BYOD, Acceptable Use, Code of Conduct, Business continuity plan, Disaster recovery plan, User management, Humen resource, vendor management, etc.
- People: security awareness training (per department), phishing drills, secure development, onboarding/offboarding process, etc.
- Consider to review NIST (National Institute for standards and technology) and/or ISO 27001 frameworks approach towards Risk Assessment
Summary:
Risk Assessment is the process of identifying, assessing, managing, and mitigating risks by applying pre-defined processes:
- Mapping and assessment of assets
- Risk worksheet (Assets, Risk, Vulnerability, Exploit, Damage value)
- Risk mitigation worksheet and plan – how to mitigate certain risks to assets based on (high, medium, low) – money, effort and time. It can mitigate with tools, technologies, processes.
- Process and Team (organization) – harness relevant stakeholders to the mission.
- Risk impact analysis and budget
- Risks and vulnerabilities are classified as High, Medium and Low
- Probability of risk being exploited also has a classification of High, Medium and Low
- Based on possible damages values and classification, risks are managed in a list and prioritize
- Management meeting – Presentation of the Organizations should have a TOP 10 list based on damage-value that is managed closely and the rest of the risks by the appropriate owned
- Documentation: How you manage it can greatly assist. Excel via google docs and 'Risk management' board in a project management tool. Every risk should have a domain, risk, mitigation plan, risk impact, owner, due date.
Startups need to manage a pro-active approach toward risk management. Not knowing your risks means you are accepting them, and probably not seeing what might come. Risk management is also an integral part of any compliance, it's only a matter of time – so start when you are small and dynamic!
Read more on Conducting a Risk Assessment: Best SOC 2 and ISO 27001 Practices




